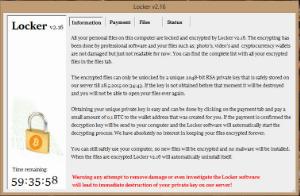
It's called Locker and has been infecting employee's workstations but sat there silently until midnight May 25, 2015 when it woke up. Locker then started to wreak havoc in a massive way.
Bleepingcomputer has a support topic that is 14 pages long and they received 100s of emails from consultants all over the world. Based on their experience with cryptoware, they stated this strain has a large "installed" base, which does not bode much good. Topics related to this new strain are suddenly posted on all the major support boards, AV forums, etc. It appears we have a new player in Ransomware City, and this looks like an 800 pound gorilla very similar to CryptoLocker. At the moment, it looks like the infection vector is exploit kits but there are rumors of a compromised MineCraft installer. Here is what it does:
- A series of Windows services are used to install Locker on the computer and encrypt data files.
- During the install process, Locker will check if the computer is virtual machine and terminate if detected.
- Encrypts data files with RSA encryption, and does not change the file extension. After the encryption it deletes your c:\ shadow volume copies and displays its ransom interface.
- If your backups failed and you are forced to pay the ransom, once payment has been confirmed the ransomware will download the private key and automatically decrypt your files.
The files that are encrypted are the following types: .doc, .docx, .xlsx, .ppt, .wmdb, .ai, .jpg, .psd, .nef, .odf, .raw, .pem, .rtf, .raf, .dbf, .header, .wmdb, .odb, .dbf, and again, Locker does not change the file extension so your users will get error messages from their applications that the file is corrupted. As you see on the screenshot, it has a scary message in red at the bottom of the screen stating: "Warning any attempt to remove damage or even investigate the Locker software will lead to immediate destruction of your private key on our server!" This is just to force you into paying, not something to be too worried about.